
Expanding Beyond Amazon: Multi-Channel …
In today's competitive e-commerce landscape, relying solely on a single sales channel like…

Enhancing Business Collaboration Throug…
Interoperability technology is crucial in modern businesses to enhance collaboration or commun…

Top 12 OCR Tools To Extract Text From I…
OCR tools are gaining popularity due to their powerful algorithms. OCR technologies can extrac…

SSL vs TLS: Decoding the Differences
SSL and TLS are cryptographic protocols gaurantee data privacy, authenticity, and integrity over a network. This post will clarify SSL versus TLS for those confused about the distinctions between the two protocols. Security is paramount in today’s digital and technological-driven world. As we transfer bulk data over the internet, pr…

7 Most Common Programming Errors Every Programmer Should Know
Every programmer encounters programming errors while writing and dealing with computer code. They may seem frustrating for novice programmers. Meanwhile, seasoned programmers are very quick at locating and fixing them. Edsger W. Dijkstra, a well-known computer scientist, said: "If debugging is the process of removing bugs, t…

Top 10 Uses Of Artificial Intelligence For Cybersecurity
The global AI in cybersecurity market, at $22.4 billion in 2023, is set for a dramatic change. Experts predict that the industry's market value will reach $ 60 billion by the year 2028. This high annual average growth rate of 21.9% shows the impressive growth trajectory of this astonishing rise. The article examines how AI s…

Gmail Mastery: Discover 15 Tips and Tricks for a Clutter-Free Inbox
Imagine you’re wading through a jungle, not of towering trees and vines, but of emails: updates, newsletters, reminders, the endless “reply-alls.” It’s a digital wilderness where important messages often get lost in the thick underbrush of spam and promotions. This is the daily reality for millions navigating the w…

What is Code Refactoring? Why Should You Consider It?
Are you seeking different ways to enhance your code? Well, the following post is definitely worth your time. Have you ever come across the term code refactoring? If not, let me explain to you what exactly code refactoring is and how it can turn out to be beneficial. Why Code Refactoring? Now, first of all, tell me something: how …

Difference Between Array and String
Many programming languages, such as C, C++, Java, etc., support an array and a string. While an array is generally considered a data structure, a string is basically a data type. They differ from each other based on their ability to store different types of data. The major difference between array and string is: While a string stores a se…
Difference Between While and Do While Loop
Loops come in handy when you want to execute the same block of code repeatedly. They help you optimize and organize your program. Among the different types of loops, the two most confusing ones are while and do-while loops. The while loop evaluates the given condition first and executes a block of code only if the cond…

Unlocking the Phases of Ethical Hacking: A Comprehensive Guide
Although the term hacking in ‘ethical hacking’ may confuse you as an illegal practice, it is not. It is simply a process of providing digital safety to your digital world. Our lives are majorly intertwined with technology. Hence, the need for opting for safe measures is crucial. As you must be aware, the cyber menaces…
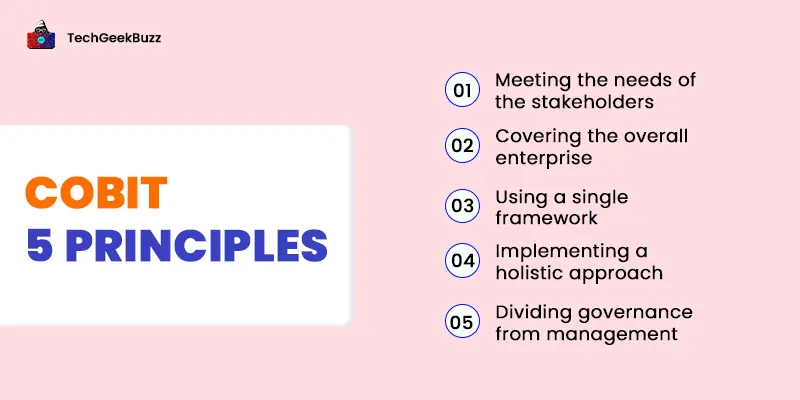
COBIT 5 Principles - Everything You Need to Know About!
Imagine a bus without a conductor. Directionless, right? To bring in order, structure, and direction, just like a bus needs a conductor, organizations need certain frameworks to manage their processes - COBIT 5! COBIT stands for Control Objectives for Information and Related Technology. COBIT 5 framework is a set of principles that foc…

10 Best Data Analytics Projects to Boost Your Data Skills
Looking for some innovative ideas for your data analytics project? Look no further! With the help of this post, explore the comprehensive list of the top data analytics projects curated specially for you! Data analytics is a vast field becoming increasingly crucial. It helps businesses perform their operations efficiently and escalat…
Top 10 IoT Projects to Learn and Master the Technology
You must have heard about the term IoT - the Internet of Things. But what is it? And how can you build some of the best IoT projects? Let’s decode it in this article. Simply put, IoT is the connection of one or multiple devices to the internet. Each device can connect and interact with each other. Do you know you are already using…

17 Best C Projects to Master the Language and Boost Your Skills
If you are looking for C project ideas, you have landed at the right place. C is simply the foundation of multiple modern languages. Many programmers use this language for its problem-solving features, versatility, and adaptability. It was created by Dennis Ritchie in 1972 at Bell Laboratories. In the initial stages, it was derived from other prog…