Continue reading below to know how to crack a zip file password in Python using Brute Force using a simple Python tutorial.
Often we have a Zip file that is encrypted with a password. To crack (find) that password, we can either use the corresponding encrypted key or continuously pass random passwords until we get the right one. This approach of trying to unlock a zip file with random passwords is known as the Brute-force approach .
Obviously, it's almost impossible to manually write and check all the random or possible passwords for an encrypted ZIP file. Rather, we can write a Python script that will try to unlock a zip file by generating the number of possible passwords for the zip file.
Here, in this Python tutorial, we will walk you through a Python program that will try to unlock a ZIP file with 10 million possible passwords.
How to Crack ZIP File Password in Python Using Brute Force?
Before we jump into the Python code implementation, let's first discuss the dependencies and library we will be using in the Python tutorial.
Dependencies and Library
-
Python zipfile Module
Python comes with the zipfile standard module or library. As the name suggests, it is used to handle zip files in Python. Consequently, using this library, we can archive, compress and extract a zip file. So, here in this Python tutorial, we will be using this library to extract our zip file. As it is a part of Python Standard Libraries, you do not need to install it.
-
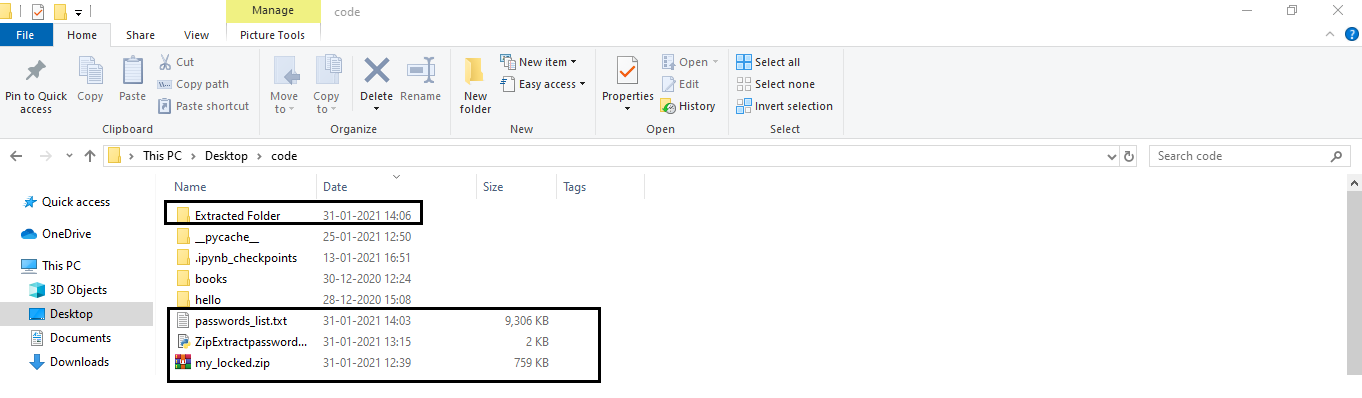
A Locked Zip File
For this tutorial, you will also require a password-encrypted zipfile. Here, we will be using the
my_locked.zip
file and it is in the same directory as that of our Python script.
-
The Passwords list txt File
In this tutorial, we will be using the Brute-force approach to unlock the
my_locked.zip
file. For that, we require the
passwords_list.txt
text file. It contains all the possible and vulnerable passwords. You can copy-paste a list of 10 million passwords from
this link
and save it locally by the file name
passwords_list.txt
.
Now that we are all set with the dependencies and library, it's time to open your best Python IDE or text editor and start coding.
How to Crack ZipFile Password and Extract Files in Python?
Step#01 - Start with importing the zipfile library in your Python script.
import zipfile
Step#02 - Now, declare two Python identifiers that represent our zip file and password list filenames.
#file names
pwd_filename = "passwords_list.txt"
zip_filename = "my_locked.zip"
Step#03
- Next, using the Python context manager or
Python file handling
, we will first open and read the
passwords_list.txt
file in binary format using the
"rb"
mode. We are reading the passwords_list.txt file in binary mode because the
extractall()
method of zipfile accepts the password in byte data or binary format.
#read passwords_list file in binary mode
with open(pwd_filename, "rb") as passwords:
#convert all the passwords into a list
passwords_list = passwords.readlines()
#total number of passwords
total_passwords = len(passwords_list)
#load zipfile
my_zip_file = zipfile.ZipFile(zip_filename)
for index, password in enumerate(passwords_list):
#try if password is correct
try:
my_zip_file.extractall(path="Extracted Folder", pwd=password.strip())
print("\n +++++++++++++++++++SUCCESS+++++++++++++++++++++++")
print("Password Found: ", password.decode().strip())
print("All Files has been Extracted inside the New DIrectory Extracted Folder")
break
#if password fails
except:
print(f"!..................................Scanning complete {round((index/total_passwords)*100, 2)}%")
print("!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!")
print(f"Trying password {password.decode().strip()} ")
print("!!!!!!!!!!!!!!!!!!!!!!!!!FAIL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!\n")
continue
Important observations:
-
The
with open(pwd_filename, "rb") as passwordsstatement will read the passwords_list.txt file in binary format. -
The
passwords_list = passwords.readlines()statement stores all the lines in thepasswords_listlist. -
total_passwords = len(passwords_list)returns the total number of passwords present in thepasswords_list. -
The
my_zip_file = zipfile.ZipFile(zip_filename)statement load themy_locked.zipfile in the Python script. -
The
tryblock containsmy_zip_file.extractall(path="Extracted Folder", pwd=password.strip()), and theextractall()function will extract all the files present in themy_locked.zipfile inpath=Extracted Folderifpwdis correct.
Now, put all the code together and execute.
#Python Program to Crack Zip File Password Using Brute Force.
import zipfile
#file names
pwd_filename = "passwords_list.txt"
filename="chromedriver_win32.zip"
zip_filename = "my_locked.zip"
#read passwords_list file in binary mode
with open(pwd_filename, "rb") as passwords:
#convert all the passwords into a list
passwords_list = passwords.readlines()
#total number of passwords
total_passwords = len(passwords_list)
#load zipfile
my_zip_file = zipfile.ZipFile(zip_filename)
for index, password in enumerate(passwords_list):
#try if password is correct
try:
my_zip_file.extractall(path="Extracted Folder", pwd=password.strip())
print("\n +++++++++++++++++++SUCCESS+++++++++++++++++++++++")
print("Password Found: ", password.decode().strip())
print("All Files has been Extracted inside the New DIrectory Extracted Folder")
break
#if password fails
except:
print(f"!..................................Scanning complete {round((index/total_passwords)*100, 2)}%")
print("!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!")
print(f"Trying password {password.decode().strip()} ")
print("!!!!!!!!!!!!!!!!!!!!!!!!!FAIL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!\n")
continue
Output
..................................Scanning complete 0.04%
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Trying password 2222
!!!!!!!!!!!!!!!!!!!!!!!!!FAIL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!..................................Scanning complete 0.04%
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Trying password 102030
!!!!!!!!!!!!!!!!!!!!!!!!!FAIL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!..................................Scanning complete 0.04%
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Trying password 252525
!!!!!!!!!!!!!!!!!!!!!!!!!FAIL!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
+++++++++++++++++++SUCCESS+++++++++++++++++++++++
Password Found: 11223344
All Files has been Extracted inside the New DIrectory Extracted Folder
To cross-check if the program extracted the file or not check the directory where your Python Script is located.
Conclusion
In this Python tutorial, you learned "How to Crack Zip File Password in Python using Brute Force." This approach will only help you if the locked file password is weak or too obvious. The above program, however, cannot crack the password if it is unique or not mentioned in the password_list.txt file.
People are also reading:
- Python Program to Find the ASCII Value of a Character
- How to Crack PDF files Passwords in Python?
- Python Program to Find the Factors of a Number
- How to Extract All Stored Chrome Passwords With Python?
- Python Program to Find the Sum of Natural Numbers
- How to Install Python 3 on Windows 10?
- Python Program to Check if a Number is Positive, Negative or 0
- Best Python Compiler
- Python Timestamp to Datetime and Vice Versa
- Time Module in Python




Leave a Comment on this Post