As more and more cyber threats continue to raise concerns, website security is more important than ever. Website owners are now more concerned with protecting their sites and visitors from malicious online behavior. Maintaining website security is crucial to protect your company's reputation, brand, and online presence and prevent financial loss and website closure. While keeping visitors and customers, you can protect your website's reputation.
So without further ado, let's take a deeper look into the concept of web security, the potential threats, and the methods to overcome them in this blog post.
What is Web Security? [Defintion]
The term Web security refers to security solutions that guard against internet-based cyber threats , such as malware, phishing, and other threats that can result in breaches and data loss for your users, devices, and more extensive networks. In simple terms, web security refers to security solutions and protocols that ensure the security of data over the web or the internet. Many web security solutions reduce the security risk to your company when users unintentionally browse dangerous files and websites.
Any business that employs computers requires web security to run smoothly. A website, or possibly your entire network, might go down if hackers get access to it or are successful in manipulating your software or systems, which would disrupt business activities.
How Does Web Security Work?
Web security is a security solution that serves as a web proxy and sits between users and the Internet. This solution may be software installed within the user's web browser, an on-premises device, a cloud-based machine, or both. However, the only thing that counts is that a worker's computer is set up to route all internet traffic through the web security system.
Today, there are numerous options, some of which are more complete than others. Web security encompasses the following technologies in a full stack:
- Secure Web Gateway (SWG)
To prevent viruses and block undesired traffic, Secure Web Gateway (SWG) offers threat protection and policy enforcement for users using the web.
- Browser Isolation
Browser isolation prevents downloading, copying, pasting, and printing data or documents by loading webpages or programs in a distant browser and only sending the user pixels.
- URL Filtering
URL filtering provides security from web-borne malware by screening and blocking inappropriate access and content.
- Firewall / IPS
Firewall/IPS offers visibility, app control, and network security. Cloud firewalls are more practical because they are always up to date and can scale to handle demand or encryption.
- Sandboxing
Software is placed in a controlled environment called a "sandbox" so that it can be scanned and run without endangering other programs or systems.
- Antivirus
Antivirus software detects and prevents Trojans, spyware, ransomware, and other harmful programs. Many services additionally offer protection against dangers like phishing, DDoS, and dangerous URLs.
- DNS Controls
DNS controls specify guidelines that regulate queries and replies about DNS traffic, enabling you to recognize and stop DNS abuses like tunneling.
- TLS/SSL Decryption
TLS/SSL decrypts incoming and outgoing communication to allow content inspection before re-encrypting it to continue to its destination.
Importance of Web Security
A web security solution offers extensive visibility and precise control over traffic headed for the internet. As it examines traffic at the application layer, its purpose and the data it carries are better understood. An organization and its people can gain from these competencies in numerous ways, including:
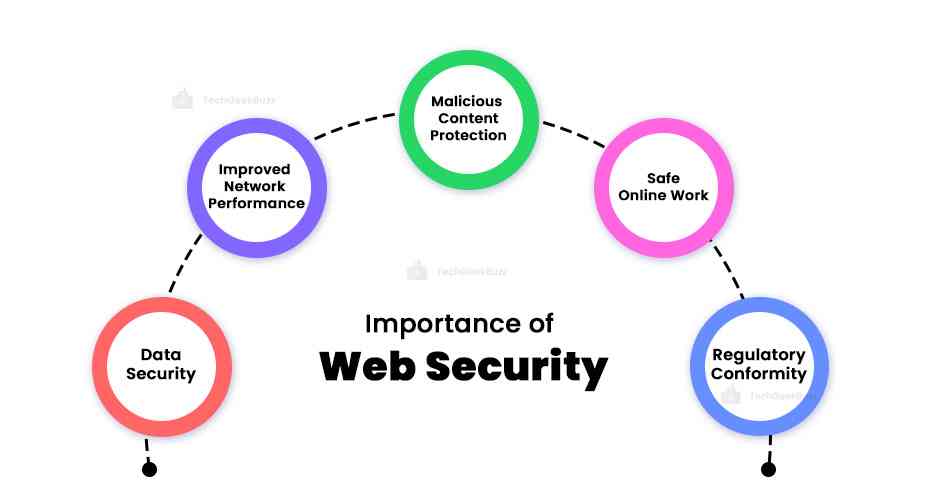
- Data Security
DLP programs keep track of sensitive data transfers inside an organization. This makes it possible to prevent exposing sensitive and priceless data to unauthorized users.
- Improved Network Performance
Application control enables network administrators to implement application-specific policies. By allowing the slowing and blocking of particular websites and traffic, the network performance for traffic from legitimate business operations is enhanced.
- Malicious Content Protection
Web security scans traffic for dangerous material and filters known-bad phishing sites and drive-by downloads. Employees are more shielded from malware and other hazards thanks to this.
- Safe Online Work
Remote workers can work safely from any location thanks to web security solutions. No matter where an employee is located, businesses may apply and enforce corporate security policies on their devices.
- Regulatory Conformity
There are more and more data protection laws that businesses must follow. Web security solutions assist in this by increasing the visibility and control of private and sensitive data held by an organization.
Threats to Web Security
A threat is a potential occurrence that could harm and damage an information system. A security threat is a risk that has the potential to hurt businesses and computer systems. Anytime a person or a company develops a website, they are open to security assaults.
The main goals of security attacks are to steal, alter, or delete a piece of private or confidential information, steal hard drive space, and get unauthorized access to passwords. Therefore, if the website you developed is susceptible to security assaults, those attacks will steal your data, manipulate your data, destroy your personal information, view your sensitive information, and even access your password.
Let's take a closer look at some of the most prevalent threats:
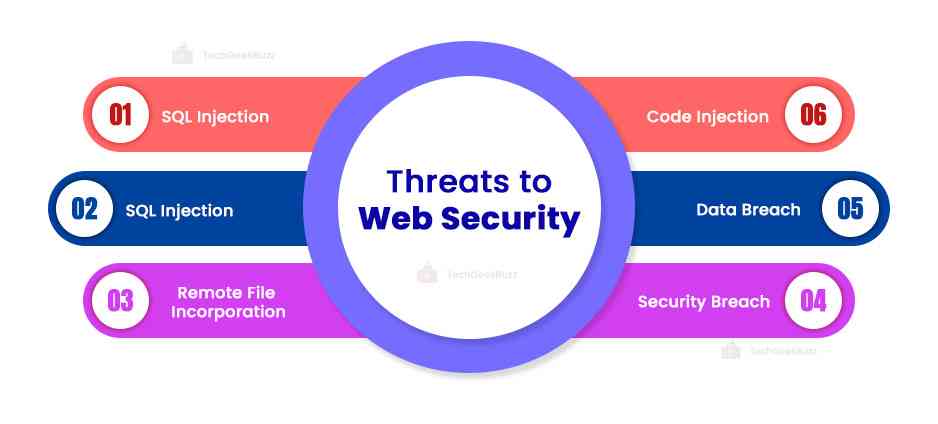
-
Injection of SQL
SQL injection allows attackers to access sensitive data, create or modify user rights, or carry out data manipulation or destruction schemes. A hacker can thus seize important data or change it to prevent or manage the operation of a vital system.
-
Cross-Site Scripting
Cross-site scripting (XSS) is the name of a flaw that allows attackers to place client-side scripts inside a web page . This is then utilized to have immediate access to crucial info. A hacker may employ XSS to impersonate another user or trick a user into exposing important information.
-
Remote File Incorporation
With remote file inclusion, an attacker uses security spots in a web application to reference external scripts. The attacker can then try to upload malware using an application's referencing feature. These malware varieties are also known as backdoor shells. Hackers carry out the entire process from a different Uniform Resource Locator (URL) on a different domain.
-
Security Breach
Password hacking is a systematic method for accessing online resources. Frequently, a hacker will use a password that a user or administrator had previously used to sign in to a different website for which the hacker has a list of login information.
-
Data Breach
An information breach occurs when the imposters make private or delicate data public. Data breaches might occasionally happen by mistake, but they are frequently the work of hackers who want to use or sell the data.
-
Code Injection
To insert and execute malicious code, an attacker must exploit a flaw in input validation in the computer's software system. This code then modifies the operation of the computer and the software.
Ways to Ensure Web Security
Website security is crucial for a website to stay accessible and safe for users. Hackers can use your website to their advantage, take it offline, and influence your online presence if you do not address the website security correctly. A hacked website may have adverse effects on the bottom line, the reputation of the company, and search engine rankings.
Web apps are now an essential part of daily life and business. They enable enterprises and individuals to streamline processes, accomplish more with fewer resources, and move much more quickly toward their goals than they did in the past.
To ensure the safety of your website or application, here are a few ways to improve your Web security:
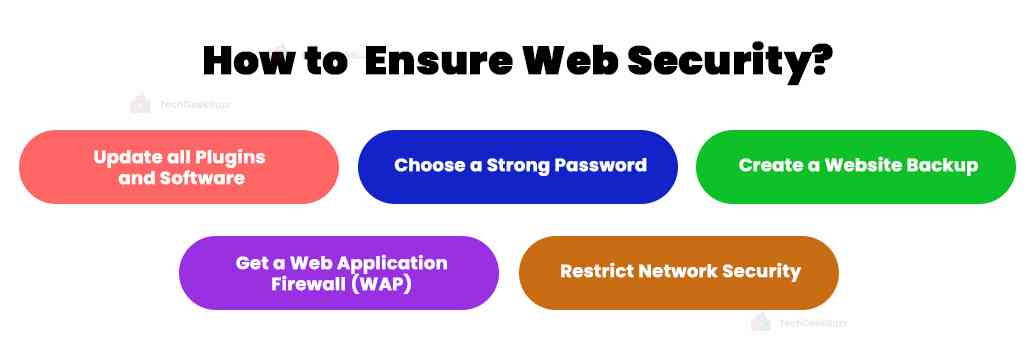
-
Update all Plugins and Software
The use of outdated software results in the compromise of numerous websites every day. Bots and potential hackers frequently scan websites for their security vulnerabilities to implement attacks. Updates are necessary to maintain your website safe and secure. You cannot maintain the security of your site if the software or apps you leverage are outdated. So, give serious consideration to any requests for the update of software and plugins.
Furthermore, updates frequently include security improvements and vulnerability fixes. Check your website for updates or install a plugin that notifies users of upgrades. Another method to guarantee website security is the ability of some systems to perform automatic updates.
-
Choose a Strong Password
It is difficult to remember all the websites, databases, and applications that demand passwords. Many individuals end up utilizing the same password across the board as a result of their difficulty remembering their login details. For each new log-in request, create a unique password. Create complicated, unpredictable, and challenging passwords.
As an option, you could create a complex password consisting of a 14-digit. Ensure to create it as a combination of letters and digits. You can later store the password(s) on a different computer, a smartphone, or an offline file.
-
Create a Website Backup
An effective backup solution is one of the most significant ways to secure your website. You ought to possess more than one. Each is essential to restoring your website following a serious security event. You can attempt to recover any deleted or damaged files in a number of different methods.
- Keep the information on your website off-site. Remember that your backups are just as susceptible to attacks as your website, so avoid storing them on the same server.
- Decide whether to save a copy of your website on a hard drive or personal computer. Find a location off-site to protect your data from viruses, hacking attempts, and hardware malfunctions.
- Creating a cloud backup of your website is an additional choice. Data may be easily stored and accessed from anywhere, thanks to cloud technology.
- You should think about automating your website backups in addition to determining where to store them. Utilize a service that allows you to plan site backups. Additionally, make sure your solution has a trustworthy recovery system.
- Make sure your backup procedure is redundant by backing up your backup.
- Leverage HTTPS and an SSL Certificate.
Having a secure URL would be beneficial in keeping your website secure. You need HTTPS, not HTTP, to provide confidential information if site users choose to send it.
What exactly is HTTPS?
HTTPS (Hypertext Transfer Protocol Secure) is a secure communication protocol to transmit data between a web server and a web browser. To put it simply, HTTPS is a secure way of communication between two different systems.
What is SSL?
Secure Sockets Layer , or SSL, is yet another essential web protocol. This exchanges visitors' data between your database and the website. SSL encrypts data in order to shield it from interception by outside parties.
-
Get a Web Application Firewall Application
Make sure you leverage a web application firewall (WAF) for your website. It sits between the data connection and the server hosting your website. The objective is to read every piece of data that passes through your website in order to defend it.
The majority of WAFs available today are cloud-based and plug-and-play services. The cloud-based WAF service serves as a gateway for all incoming traffic and guards against hacker attempts. Additionally, it filters out unwanted traffic like spammers and harmful bots.
-
Restrict Network Security
You should evaluate your network security after you believe your website is secure. Employees accessing your website on office laptops could unintentionally open up a dangerous gateway.
Consider implementing the following at your company to stop them from granting access to the server hosting your website:
- Make computer logins disappear after a brief inactive period.
- Ensure that your system informs users every three months to change the password.
- Every time a device connects to the network, make sure to scan it for malware.
What Protection Does Web Security Provide?
Web security is crucial, but it's difficult to safeguard against threats daily. When attempting to defend the web, IT security departments encounter various obstacles, such as blocking assaults and coping with resource and talent limitations.
To manage email and online security in the past, security teams installed various on-premises systems. However, enterprises are increasingly relying on all-encompassing email and online security solutions - via integrated, cloud-based technologies that make the process easier and lower the cost of risk reduction. A seamless and scalable solution for defending both is crucial because attackers frequently utilize email and online channels together.
Security Offered by Web Security
Web security shields an enterprise from some of the most prevalent online risks. Let’s take a look at a few of them:
-
Phishing Tactics
Phishing is a strategy that hackers leverage to trick people into giving confidential information. They might use emails to accomplish this or create fake websites that mimic actual ones. The user subsequently submits confidential information onto the bogus website, making it accessible to the attacker.
-
Session Hijacking
When a user's session is hijacked, an attacker can act on a website under that user's guise. The attacker can conceal their identity and potentially get away with any illegal activity they engaged in while on the website because it looks that the user is the one carrying out the actions.
-
Theft of Data
Attackers frequently attempt to steal data to access email accounts, payment systems, and other websites or applications that require authentication. Hackers occasionally utilize the data for their purposes but may sell it to someone else.
-
SEO Spam
Attackers may utilize erroneous links, comments, or pages on a website in search engine optimization (SEO) spam attacks to divert users or direct them to harmful websites.
-
Malicious Links
Harmful redirection links users to malicious websites they had no intention of visiting. The user's computer may become infected with malware after visiting this site.
Best Web Security Defense Techniques for Developers
-
Web Monitoring
Web scanning is crawling a website with an application to look for flaws that could make it vulnerable to bot, spyware, rootkit, Trojan horse, or distributed denial-of-service (DDoS) attacks. The scanner goes over each page of the website, creating a structure-filled diagram that shows how the site is organized. The entire website is then thoroughly examined for any potential flaws.
-
Resource Allocation
A developer uses a resource assignment approach to designate the required resources to keep them informed of any new problems as they appear. With regular updates, the developer may spot dangers and counter them before security is indeed penetrated.
Conclusion
Website security is becoming more crucial as more sophisticated cyber threats emerge because website owners are more concerned with safeguarding their sites and users from harmful cyber activity. Therefore, maintaining website security is essential to preserving your company's reputation, brand, and online presence and avoiding financial loss and website shutdown. You will be able to maintain visitors and clients while safeguarding the importance of your website.
We hope this blog has helped you gain insights regarding Web Security, the possible threats it causes, and the significant measures required to safeguard the data and systems.
Happy Reading!
People are also reading:
![What is Web Security? [Definition, Importance, & Threats]](/media/new_post_images/What_is_Web_Security.webp)



Leave a Comment on this Post