Companies rely on the cloud computing model in this digital era for better optimization and results. But, what is cloud computing ? It refers to the on-demand delivery of computing services, such as networking, storage, analytics, databases, servers, and software.
Thanks to cloud computing, your business may communicate and share information more easily outside the usual channels. It increases employee cooperation by allowing several users to exchange and work together on data and files simultaneously. But with this massive increase in cloud-based solutions, it is crucial to understand the security requirements for protecting data.
Cloud security should be an essential element of your business. Cloud infrastructure, which covers many industries and verticals, underpins almost every aspect of modern computing. Through this article, we aim to help you understand how you should incorporate cloud security into your business and what threats you may encounter.
So, let's begin our discussion.
What is Cloud Security? [Definition]
Cloud security, also referred to as cloud computing security, is a collection of laws, regulations, practices, and technological advancements that work together to protect the systems, data, and infrastructure hosted in the cloud. These security measures aim to protect cloud data, aid in regulatory compliance, protect consumer privacy, and provide authentication guidelines for specific users and devices.
We can customize cloud security to fit the needs of the business, from access verification to traffic filtering. Because these cloud security rules can be developed and managed in a single location, administration costs are also reduced, and IT teams have more time to focus on other business areas.
Components of Cloud Security
Now, we will take a look at the components of cloud security. The entire suite of cloud security is designed with the intent to protect the following:
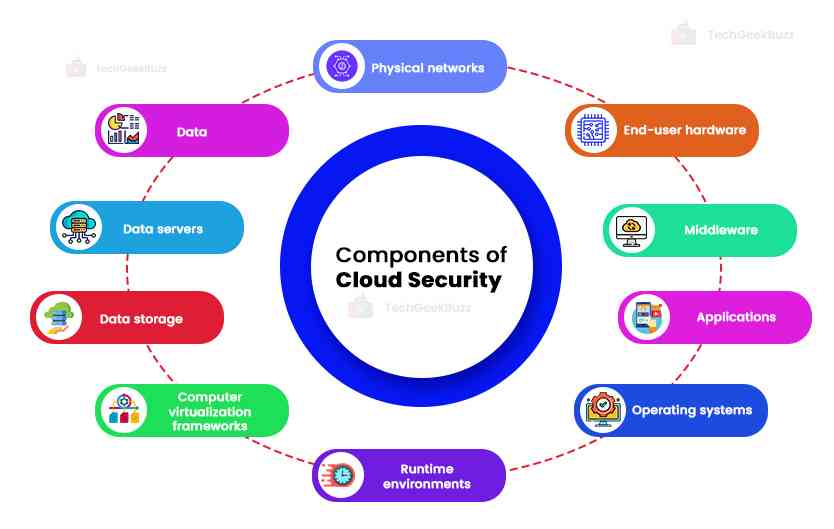
- Physical networks such as routers, electrical power, cabling, etc.
- Data - all the information stored, edited, and accessed
- Data servers - core network computing software and hardware
- Data storage - hard drives, etc.
- Computer virtualization frameworks - virtual machine software, guest machines, and host machines
- Runtime environments - execution and upkeep of a running program
- Operating systems (OS) - software that houses
- Applications - traditional software services ( tax software, emails, productivity suites, etc.)
- Middleware - application programming interface (API) management.
- End-user hardware - mobile devices, computers, Internet of Things (IoT) devices, etc.
In cloud computing, the ownership of various elements might vary substantially, which affects the scope of client security. It is essential to understand how these elements are commonly combined since the way the cloud is protected can vary based on who controls each component.
Securing cloud computing components involves two main perspectives, as follows:
1. Cloud Service Types
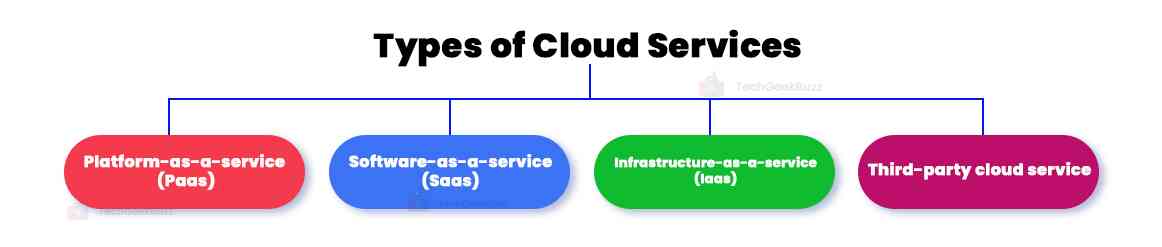
Third-party suppliers offer several cloud service types as the building blocks of cloud environments. You may control the service's components to varying degrees depending on the kind of service:
-
Third-Party Cloud Service
It involves the management of the provider of the physical network, data servers, data storage, and virtualization software. Through virtualization on the provider's servers and delivery via their in-house managed network, clients can access the service remotely. To provide users with access to their cloud needs from anywhere with internet connectivity, hardware and other infrastructure costs are offloaded.
-
Platform-as-a-service(Paas)
When clients use cloud services, they host their programs on provider servers, which they then operate from within a sandboxed environment. Providers manage the operating system, middleware, and runtime. The client is responsible for managing client applications, data, access control, end-user devices, and networks. Windows Azure and Google App Engine are examples of PaaS.
-
Software-as-a-service(Saas)
A cloud service provider offers clients access to programs that it solely hosts and operates on its servers. It manages the applications, middleware, runtime, and operating system. Clients' only responsibility is obtaining their applications. Google Drive, Slack, Cisco, Microsoft 365, Salesforce, and Evernote are a few instances of SaaS.
-
Infrastructure-as-a-service(Iaas)
Customers using cloud services can host most of their processing on hardware and distant connectivity frameworks, even down to the operating system. Providers manage only essential cloud services. It is the responsibility of the clients to secure all components placed on top of an operating system, such as applications, middleware, runtimes, data, and the OS itself. Also, clients must manage user networks, end-user devices, and access rights. Examples of IaaS include Amazon Web Services (AWS), Google Compute Engine (GCE), and Microsoft Azure.
2. Cloud environment
They are the models for deployment where one or more cloud services build a system for companies and end users. This divides management duties between clients and providers, which also includes security.
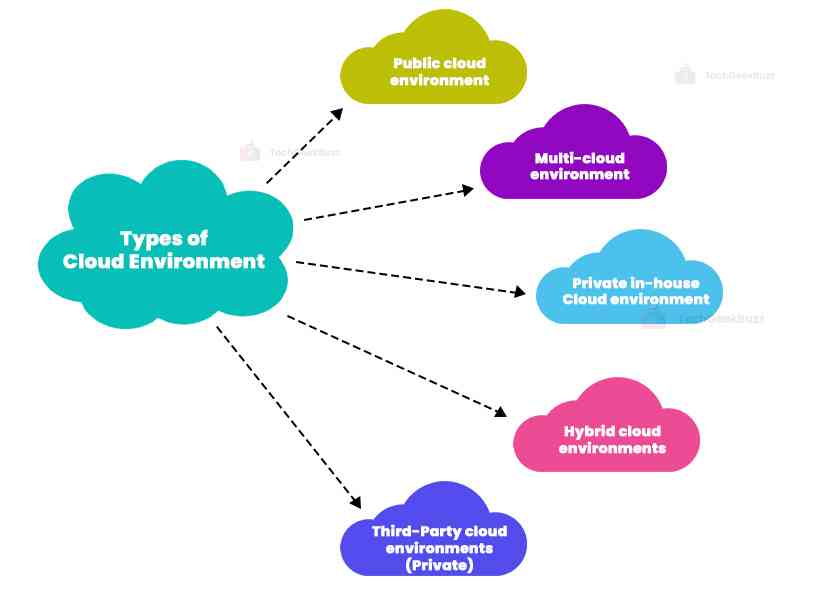
The cloud environments that we currently use are:
- Third-Party Cloud Environments (Private): They rely on a cloud provider that gives clients exclusive access to their cloud. Typically, an outside supplier owns, manages, and operates these single-tenant environments remotely.
- Public Cloud Environments : They include multi-tenant cloud services, such as office buildings or coworking spaces, where a client uses a provider's servers with some other clients. These are third-party solutions that the provider manages to offer customers with access online.
- Multi-cloud Environments : These are implemented using two or more cloud services provided by various providers. It is possible to use these with any combination of public and private cloud services.
- Private in-house cloud Environments : These are additionally made up of servers for single-tenant cloud services but run from separate private data centers. In this instance, the company manages the cloud environment directly, allowing for complete element setup and configuration.
- Hybrid Cloud Environments : They integrate one or more public clouds with a private cloud from a third party and an on-site data center.
Through this classification, we can see that cloud-based security may differ for different users or clients depending on the cloud area users are operating in. However, both individual clients and clients from organizations gain similar benefits from it.
Cloud Security Risks
So far, we have understood what cloud security is and what its components are. But still, we don't know about the security issues of cloud computing. And it is impossible to defend ourselves against something we don't know about. The lack of adequate cloud security can open users and providers to various online dangers. Typical challenges to cloud security include:
- Human error-related internal risks include improper user access control configuration.
- Incompatibility with conventional IT frameworks and interruptions to third-party data storage services are some drawbacks of cloud-based infrastructures.
- Hackers cause external dangers like malware, phishing, and DDoS attacks.
One of the significant issues the cloud faces is the absence of a perimeter. The perimeter was the emphasis of traditional cyber security. However, cloud systems are extensively networked, making account theft and unsecured APIs (Application Programming Interfaces) serious issues. Cyber security experts must adopt a data-centric strategy in light of the security dangers associated with cloud computing.
An essential factor in cloud services is that a third party stores your data, and you need to access it online. If the third party stops the services for any reason, you will not be able to access your data. For example, a phone network failure can prevent you from using the cloud at a crucial moment. On the other side, a power outage can affect the data center where your data is stored, possibly leading to a loss of that data forever.
Interconnectedness also creates problems for networks. Hackers frequently target networks that have weak or compromised credentials. After landing safely into a network, a hacker may immediately disperse and use shoddy cloud interfaces to look for data across several databases or nodes. They can even export and store any stolen data on their cloud servers. Cloud security must go beyond merely securing access to your cloud data.
A cloud security strategy's objective is to assuage the threat provided by these risks by safeguarding data, controlling user authentication and access, and continuing to function in the event of an attack.
How Does Cloud Security Work?
Cloud security works in the manner through which it can tackle the risks that come with cloud computing. Every measure taken is to achieve the following goals:
- Preventing carelessness or human error that results in data leaks.
- Defend networks and storage against nefarious data theft.
- Minimize the effects of any system or data compromise.
- In the case of data loss, plan for data recovery.
In order to achieve the goals mentioned above, let's take a detailed look at what steps we must take:
-
Identity and Access Management(IAM)
IAM relates to the rights granted to user accounts in terms of accessibility. Managing user account authorization and authentication also applies here. Access controls prevent excellent and bad users from accessing and compromising critical data and systems. IAM encompasses techniques like password management and multi-factor authentication, among others.
-
Governance
This focuses on processes for threat detection, prevention, and mitigation. Threat intelligence may help SMBs and organizations track and prioritize threats to maintain the strict security of essential systems. However, emphasizing safe user behavior norms and training may benefit individual cloud customers. Although these are particularly important in professional settings, knowing the safe use recommendations and how to handle hazards is helpful for all users.
-
Data Security
It is a part of cloud security that involves preventing threats on a technological level. Providers and clients can erect barriers to prevent sensitive data from being accessed or seen using tools and technology. One of the most effective tools out of those is encryption. Your data is encrypted, so only a person with the encryption key can decode it. The loss or theft of your data will result in its illegibility and ineffectiveness. In cloud networks, emphasis is also placed on security measures for data transit, such as virtual private networks (VPNs).
-
Data Retention(DC) and Business Continuity(BC) Planning
This entails technical steps for disaster recovery in the event of data loss. Any DR and BC plan should include techniques for data redundancy, such as backups. Having technical systems in place to guarantee continuous operations might also be beneficial. For a complete BC plan, frameworks for validating backups and adequate employee recovery instructions are just as important.
-
Legal Compliance
It centers around upholding user privacy standards established by governing agencies. Governments are aware of how important it is to stop the commercial exploitation of private user data. Organizations must, therefore, adhere to rules to uphold these policies. Data masking is one strategy that hides identity within data through encryption techniques.
These are some of the steps that are taken to ensure cloud security.
Importance Of Cloud Security
In the era of cloud technologies, everyone has reevaluated their understanding of cyber security . While switching between local and remote PCs, your data and programs might always be accessible via the Internet. If you use Google Docs on your smartphone or Salesforce software to manage your customers, that information could be kept everywhere. It is more difficult to defend it than when all that was required was to stop unauthorized users from accessing your network. Prior IT practices must be modified for cloud security. Working with a cloud provider who provides best-in-class safety tailored for your infrastructure is crucial.
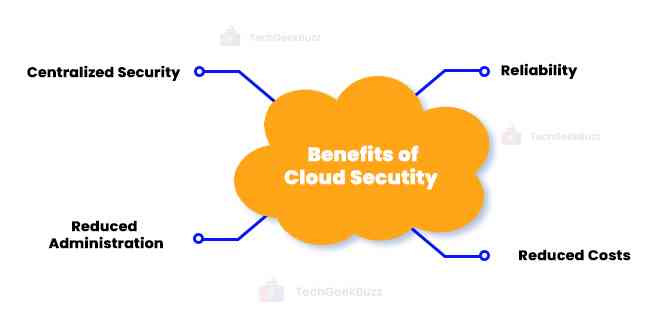
Working with cloud security has additional advantages, including the following:
-
Centralized Security
Cloud security centralizes security in the same way cloud computing centralizes programs and data. Managing many devices and endpoints that make up cloud-based company networks can be challenging when dealing with BYOD or shadow IT.
Moreover, centralized security simplifies the monitoring of network events and improves traffic analysis and web filtering, and hence, there are fewer software and policy upgrades due to managing these entities centrally. Having a single point of contact for disaster recovery can make it easier to create and implement plans for the same.
-
Reduced Administration
Manual security setups and nearly continual security upgrades become history when you select a trustworthy cloud services provider or cloud security platform. When you move these tasks to the cloud, security administration is taken care of on your behalf in a single spot, even though they might be resource-intensive.
-
Reduced Costs
One advantage of using cloud security and storage is that it eliminates spending money on specialized hardware. This lowers administrative costs in addition to reducing capital expenses. Cloud security offers proactive security features that provide protection around-the-clock with little to no human interaction, replacing IT teams' reactive firefighting of security concerns in the past.
-
Reliability
Services for cloud computing provide the highest level of dependability. Users can securely access data and applications stored in the cloud from any location or device with the proper cloud security measures.
Threats can affect any cloud computing architecture. The correct security provisions must be in place if you run a native cloud, hybrid cloud, or on-premise environment. Cloud security provides all the features of traditional IT security. It enables companies to use the many benefits of cloud computing while remaining safe and compliant with all legal and regulatory obligations.
Cloud Security Challenges
The absence of distinct perimeters in the public cloud causes difficulties securing the environment. Using modern cloud approaches like automated Continuous Integration and Continuous Deployment (CI/CD) methods, distributed serverless architectures, and transitory assets like Functions as a Service and containers renders this even more challenging.
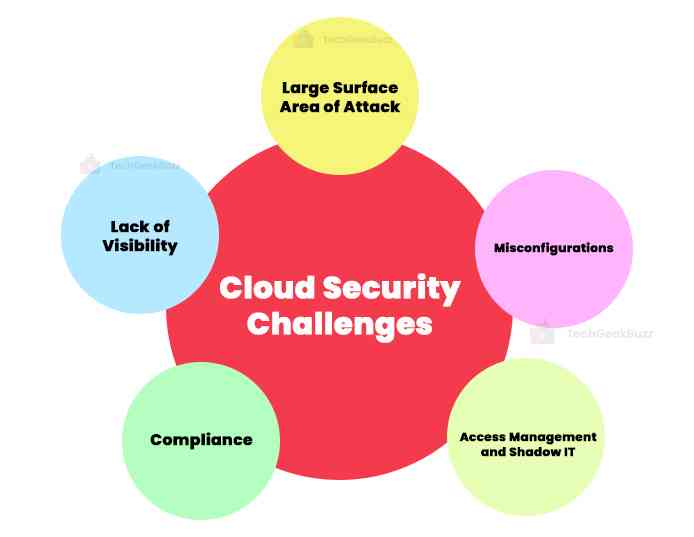
Some of the significant cloud security challenges are:
-
Large Surface Area of Attack
In order to access and disrupt workloads and data in the cloud, hackers are increasingly using the public cloud environment as a big and substantial attack surface. They do this by taking advantage of unprotected cloud ingress ports. Several malicious cyber threats , including malware, zero-day vulnerabilities, account takeovers, and others, are now commonplace.
-
Lack of Visibility
Because many cloud servers are managed outside corporate networks and via third-party companies, losing track of how and by whom your data is being viewed can be simple. Customers that utilize the cloud as a result typically have difficulties in effectively identifying and measuring their cloud assets as well as in visualizing their cloud settings.
-
Compliance
The management of regulatory compliance for businesses using public or hybrid cloud deployments can occasionally lead to complexity. Relying heavily on third-party services to manage data privacy and security could lead to costly compliance issues because the organization is still ultimately accountable for these issues.
-
Access Management and Shadow IT
Businesses may be able to control and limit access points for systems installed on-site, but doing so in cloud settings can be difficult. This might be dangerous for businesses that don't have to follow BYOD rules and allow unlimited access to cloud services from any system or place.
-
Misconfigurations
In 2022, 79% of data breaches involved misconfigured assets, making the accidental insider a significant problem for cloud computing settings. Misconfigurations might occur when the proper privacy settings are not created or administrative passwords are left in place.
Cloud Security Solutions Available
In this section, we will look at some possible cloud solutions present for us.
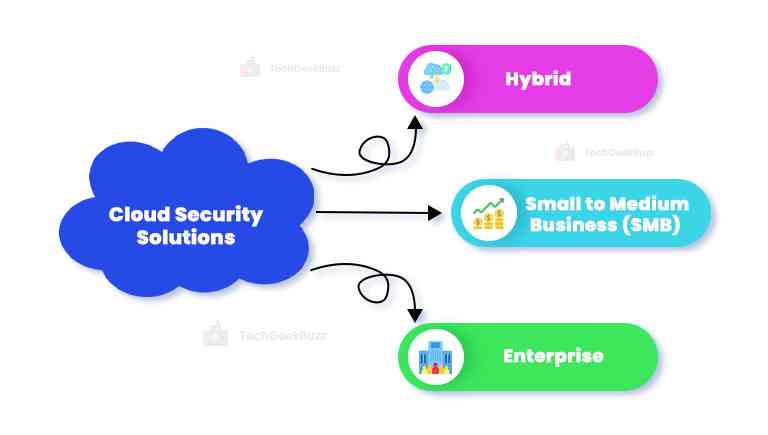
1. Hybrid Security Solutions
Hybrid cloud security services could be a brilliant choice for customers in the SMB and enterprise sectors. They are particularly beneficial in SMB and commercial applications because they are often too complex for personal use. Nevertheless, these companies may gain from the cloud's accessibility, size, and on-site control of some data.
The benefits of hybrid security solutions include:
- Segmentation of Services
This can aid a company in controlling how its data is accessed and kept. You can layer your security effectively by, for instance, storing more sensitive information locally while moving other data, applications, and processes to the cloud. Separating data can also help your company better adhere to legal requirements for data compliance.
- Redundancy
Organizations can accomplish redundancy through hybrid cloud environments. Organizations can maintain operations if one data center is taken offline or attacked with ransomware by using daily operations from public cloud servers and backing up systems in local data servers.
2. Small to Medium Business (SMB) Cloud Security Solutions
Businesses can insist on a private cloud, which is like having your own office or campus in the internet age, but individuals and smaller companies must make do with public cloud services. This is comparable to renting an apartment building with hundreds of others or using a serviced office. Your security must, therefore, be of the top priority.
You will find that the public providers you use for small- to medium-sized business apps are primarily responsible for cloud security.
However, there are some steps you can take to protect yourself:
- Multi-tenant data segmentation: Businesses must ensure that no other cloud vendor customers may access their data. Make sure segmentation mechanisms are in place, whether the data is stored on segregated servers or is carefully secured.
- Scaling cloud systems with caution: Ensure that security takes precedence over convenience when implementing cloud systems. Cloud services tend to spread out and become unregulated swiftly.
- Legal data compliance : Maintaining compliance with international laws, such as GDPR, is essential to avoiding costly fines and reputational harm. Make sure your company gives priority to techniques like data masking and the identification of sensitive data.
- Controls over user access: Managing permissions may require restricting user access to an uncomfortable level. However, starting with rigorous rights and working backward to establish a balance can be much safer than letting free permissions spread throughout your network.
3. Enterprise Cloud Security Solutions
Over 90% of larger businesses today employ cloud computing, so cloud security is essential to corporate cyber security. For businesses at the corporate level, private cloud services and other expensive infrastructure may be useful. You would still have to make sure that your internal IT team keeps your network's whole surface area up to date.
If you invest in your infrastructure, cloud security for large-scale enterprise use can be much more adaptable.
There are a few crucial things to bear in mind:
- Manage your accounts and services actively . If you stop using a service or piece of software, make sure to shut it off properly. Hackers can quickly access a cloud network's complete infrastructure, thanks to unpatched vulnerabilities, using old, inactive tabs.
- Multi-factor authentication (MFA ): This can be a password and a different code transmitted to your mobile device or biometric information like your fingerprints. Although time-consuming, it is beneficial for your most private data.
- Analyze the hybrid cloud's costs and benefits : Segmenting your data is much more crucial since you will work with more data for enterprise use. Whether logically separated for separate storage or individually encrypted, you must ensure that your data is distinct from that of other customers. This is where hybrid cloud services can be helpful.
- Be aware of shadow IT : It's crucial to train your staff to refrain from using illegal cloud services on your networks or for business-related tasks. Your company may be vulnerable to malevolent actors or legal problems if critical data is transmitted through unsafe networks.
Therefore, it is crucial to ensure that your network and devices are as secure as possible, regardless of whether you are an individual user, SMB user, or even an Enterprise level cloud user. This begins with each user having a solid awareness of fundamental cyber security.Additionally, you must make sure that a trustworthy cloud-based security solution is protecting your network and all connected devices.
These are some of the present cloud security solutions. These solutions help enhance cloud security and provide a better user experience.
How to Secure Cloud?
Thankfully, there are many things you can take to protect your data in the cloud. Let's look at a few of the standard techniques:
-
Encryption
It is among the most excellent strategies to protect your cloud computing infrastructure. There are numerous ways to use encryption, and they might be provided by a cloud provider or by a different company that offers cloud security solutions:
- Encryption of all communications with the cloud.
- Encryption of very private data, such as login passwords.
- Encryption from beginning to end for all data uploaded to the cloud.
Either you encrypt your data before uploading it to the cloud yourself, or you utilize a cloud provider who will do so for you as part of the service. End-to-end encryption may be excessive if all you plan to store in the cloud is non-sensitive data like films or corporate images. On the other hand, it is essential for financial, private, or commercially sensitive information.
If you use encryption, remember how important it is to manage your encryption keys safely and securely. Keep a backup of your keys, but ideally, don't store them in the cloud. Additionally, you might want to routinely update your encryption keys to ensure that anyone who obtains them is locked out of the system when you make the switch.
-
Configuration
This is yet another effective technique for cloud security. Fundamental flaws like incorrect configuration lead to a lot of cloud data breaches. You significantly reduce your danger to the safety of the cloud by avoiding them. You might want to think about working with a different cloud security solutions provider if you don't feel comfortable handling this independently.
Few principals you can follow:
- Never stick with the default settings. A hacker gains front-door access by using the default settings. Avoid doing this to make it more difficult for hackers to access your machine.
- Never leave a bucket of cloud storage open. Hackers might be able to view the content of an empty bucket by just visiting the storage bucket's URL.
- Use security protections that you can activate if the cloud vendor provides them. You run the chance of injury if the wrong security options are chosen.
-
Storage and File Sharing
For instance, you may need to carefully consider how you share cloud data with others utilising cloud-based services if you work as a consultant or freelancer. Sharing files with clients using Google Drive or another service may be simple, but you should double-check how you handle permissions. After all, you'll want to make sure that various clients are unable to view or change each other's files or folders.
Do not forget that a lot of commonly used cloud storage providers do not encrypt data. Before uploading the data, you must encrypt it yourself using encryption software if you wish to keep your data secure. Then, for your clients to be able to read the files, you will need to provide them with a key.
-
Cloud Provider's Security
Security should be one of your top priorities when selecting a cloud security service. Because cloud security providers must contribute to developing a secure cloud environment and share responsibility for data protection, your cyber security is no longer only your duty.
You can feel more confident that your cloud assets will be secure if you receive the proper responses to three simple questions. You will also be aware of whether your supplier has adequately handled the apparent concerns about cloud security. We advise enquiring about the following issues with your cloud service provider:
- Safety audits: "Do you often have outside auditors review your security?"
- Retention of user data: "Will my data be appropriately removed if I stop using your cloud service?"
- Does our data have encryption? How much of it is encrypted?
- What policies are in place for the retention of client information?
- Management of access: "How are access permissions managed?"
- Data segmentations: "Is consumer data maintained separately and logically segmented?"
Make sure you are aware of all the services utilized by your provider. Your files may likely be kept on Amazon's servers if stored on Dropbox or backed up on iCloud (Apple's cloud storage service). As a result, you must examine both AWS and the service you are currently utilizing.
These are some of the primary measures that an individual or an organization should take to ensure the security of their data.
Conclusion
In this blog, we have discussed everything related to Cloud Security, its benefits, the importance of Cloud security, the challenges, and its solutions, so that you make an informed choice in protecting your data and business.
As companies implement these concepts and enhance their operational strategy, new challenges in striking a balance between security and productivity levels emerge. To strike the right balance, it is essential to comprehend how modern businesses may benefit from utilizing connected cloud technology while putting the greatest cloud security measures in place.
People are also reading:
![What is Cloud Security? [Importance, Challenges, and Solutions]](/media/new_post_images/Cloud_Security.webp)




Leave a Comment on this Post