The steady rise of cyber crimes and data privacy issues has affected many companies, including some big players like Uber and eBay. Therefore, securing websites and databases has become a need rather than just an option. To solve this problem we come up with the best hacking tools. To achieve a high level of data security, companies are involved in a lot of practices. One of them is ethical hacking. Also known as penetration analysis or intrusion testing, this is a practice to detect the level of protection a website has. It is achieved by doing authorized bypassing of system security to identify the potential vulnerabilities, data breaches, and threats in a network. Usually performed by companies themselves, this is a planned, approved, and above all, a legal process. The one who owns the network or system allows cybersecurity experts to test their system’s defenses.
Yes, Ethical Hacking Is Legal!
The first thing that comes to mind after hearing the word "hacking" is malicious cyber attacks. But that’s not the complete picture. Mistakes made by programmers while developing software, technically known as security vulnerabilities, is where hackers attack to penetrate the security framework of the software. If it is done to test and improve the security of some software, then it’s known as ethical hacking , which is completely legal . But if it was done by a third-party to steal the information, money, or getting access to free services, then it’s called black-hat hacking , which is illegal. Programs designed to find and exploit the loopholes and weaknesses in a system are known as hacking tools . This blog features a list of the top 10 best ethical hacking tools that you can use to test the defenses of your business security measures.
10 Best Ethical Hacking Tools
Here’s the list for a quick reference:
- John The Ripper
- NMAP
- Nessus
- Kismet
- SQLmap
- Netsparker
- Wireshark
- Nikto
- Acunetix
- Metasploit
1. John The Ripper
https://www.youtube.com/watch?v=iL2sbAKaBOY It is one of the most popular and free ethical hacking tools, which specializes in password cracking. It is best known for detecting the password cracking algorithm and preparing accordingly, resulting in efficient defenses that change dynamically based on the type of attacks performed. Moreover, John The Ripper combines several password crackers into one package. It automatically detects password hash types and includes a customizable cracker. The main features of this ethical hacking tool are:
- Magnificent in cracking encrypted passwords.
- Performs dictionary attacks .
- Efficiently includes various password crackers in a single package.
- Extremely fast in password cracking.
- Compatible with Windows, Linux, and macOS.
You can signup here .
2. Nmap
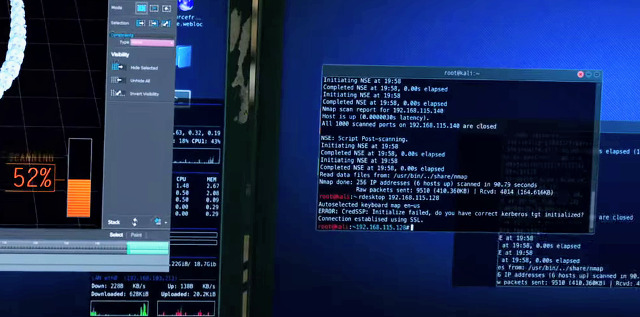
Nmap, a contraction for Network Mapper, is a free and open-source utility used for network exploration and security auditing. It runs smoothly on Linux, macOS and Windows. Nmap is useful for tasks such as network inventory, managing service upgrade schedules, monitoring hosts, and detecting SQL injection and XSS. Although best known for scanning network, this hacking tool is also proficient in:
- Detecting hosts available on the network.
- Detecting the services offered by those hosts and operating systems they are running on.
- Identifies the type of firewalls in use or similar characteristics.
You can signup here .
3. Nessus
https://youtu.be/aZgAjBnPTAc This top free hacking tool is recommended for non-enterprise usage and it works with a client-server framework. Nessus is compatible with all the major operating systems, like Windows, Kali Linux, macOS, Debian, and Ubuntu. Nessus can also perform password dictionary attacks. Other main features of the ethical hacking tools are lined-up below:
- Good at scanning remote vulnerability.
- Takes care of unpatched services and misconfiguration.
You can signup here .
4. Kismet

Mainly known for testing wireless networks, Kismet is a network detector, packet sniffer, and intrusion detection system. It works with any wireless card that supports raw monitoring code, collects packets, and detects non-beaconing and hidden networks with the help of data traffic. It is often used for RFMON mode , which means that a user will be able to monitor traffic and identify wireless networks without being associated with an access point. This program works efficiently with Linux, FreeBSD, NetBSD, OpenBSD, and macOS, but it is not always compatible with Microsoft Windows i.e. you might run into compatibility issues while using Kismet on Windows.
- You can use it to identify potential target wireless networks.
- Allows individuals to use “RFMON” or ”radio frequency monitoring” mode.
- Comes with a fast and powerful user interface.
- It captures packets without leaving any signs that it is in use
You can signup here .
5. SQLmap
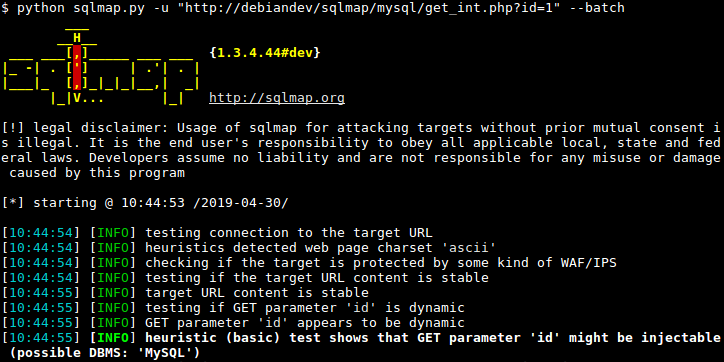
SQLmap is a robust penetration testing tool that automates the detection of SQL injection and servers that are taking over the database. Also, this tool allows you to test different types of SQL-based vulnerabilities to harden up the defense of your apps and servers, or to report vulnerabilities to different companies. The main features of SQLmap are jotted down below, have a look:
- Reduces manual work with automatic code injection capabilities.
-
Wide range of database server support:
- Oracle,
- PostgreSQL,
- MySQL and MSSQL,
- MS Access,
- DB2 and Informix.
- It is open-source and provides cross-platform functionality.
- Recognizes password hash quickly.
You can signup here .
6. Netsparker
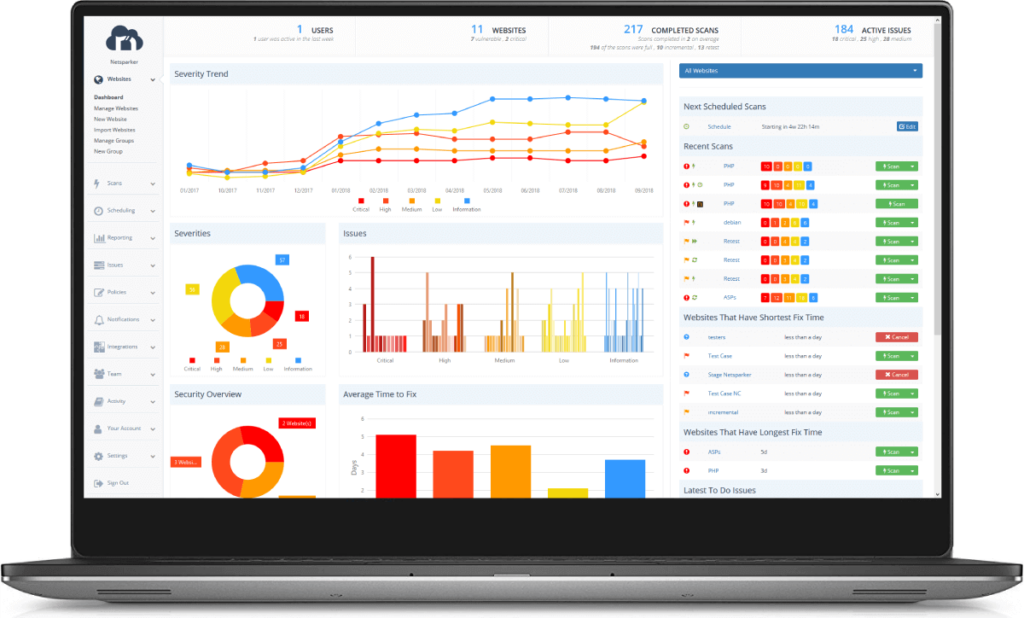
Netsparker is an easy-to-use ethical hacking tool that is utilized as a security scanning software that automatically finds SQL Injections, XSS, and other types of vulnerabilities in a web API . The ethical hacking tool comes as both, a Windows software and an online service through which you can automatically detect vulnerabilities that are mostly accurate. This will save you sitting for hours and verifying them manually. Its main highlights are:
- 100% accurate vulnerability detection with the unique Proof-Based Scanning Technology.
- Extremely fast. It can scan 1,000 web applications in just 24 hours.
- Offers integration capabilities to enhance the functionalities.
- Embedded with pent testing tools.
You can signup here .
7. Wireshark
https://youtu.be/JujID5KSdrE This widely-used hacker tool is a GTK+ -based network protocol analyzer that lets you capture and surf the contents of network frames. Wireshark can perform deep inspection of many protocols because it analyzes and captures the packets. Wireshark is embedded with a lot of features, like deep network inspection, live capture followed by offline analysis, a standard three-pane packet browser, rich VoIP analysis, readable network data, global coloring rules, and simple reports. Have a look at its other features:
- Decompresses gzip files on the fly.
- Efficiently decrypts protocols like IPsec, ISAKMP, and SSL/TLS, et cetera.
- Enables users to browse the captured network data using GUI or TTY-mode TShark utility.
- Coloring rules can be applied to the packet list for quick, intuitive analysis.
- It comes with the most powerful display filters in the industry.
- Runs on all the major operating systems.
You can signup here .
8. Nikto
https://www.youtube.com/watch?v=7XTXH5LaNU0 Nikto is a popular security tool that scans and tests several web servers to identify the software that is outdated, dangerous CGIs or files, and other issues. It is a free-to-use tool that utilizes cookies to make server-specific as well as generic checks. It has a clean and simple command-line interface that makes it easy to use and launch any vulnerability testing against your target. The main features of Nikto are mentioned below:
- Checks web servers, plugins and identifies dangerous files, outdated versions, and misconfigured files.
- Automatically identifies default installation files on any OS.
- Detects outdated software applications.
- Integration support for Metasploit Framework.
- Performs cross-site scripting vulnerability tests.
-
Provides options to export results in 3 forms:
- Plain text,
- CSV, andHTML.
You can signup here .
9. Acunetix
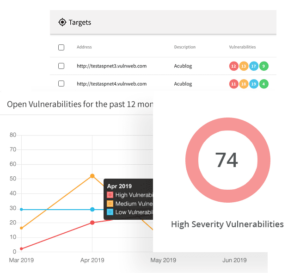
It is a fully-automated ethical hacking tool that scans any website or web application that is accessible via a web browser and uses the HTTP/HTTPS protocol. Acunetix has strong and quick solutions to analyze complex web apps and custom web apps built on Javascript, AJAX, etc. The main features of this ethical hacking tool are outlined as follows:
- Efficiently scans SQL Injection, XSS, and 4500+ additional vulnerabilities.
- Easily detects 1,200 WordPress core, theme, and plugin vulnerabilities.
- Crawl thousands of pages quickly without any interruptions.
- Smooth integration with popular WAF (Web Application Firewall) and Issue Trackers to aid in the SDLC (Software Development Lifecycle).
- Comes on-premises as well as a cloud solution.
You can signup here .
10. Metasploit
https://youtu.be/cYtDxfKdlqs Metasploit is one of the few ethical hacking tools that is used by beginners to practice their skills. It is an open-source cybersecurity project through which infosec professionals test through different penetration tools to discover vulnerabilities in software. The cybersecurity project is also used to execute remote attacks, evade detection systems, and run security scans. Metasploit comes in free and commercial editions, It can be used with a command prompt or with a web UI. The main features of this ethical hacking tool are jotted down below,:
- Efficient penetration testing.
- Helps in developing IDS signature.
- You can build security testing tools with it.
- Allows individuals to perform basic tests on small networks.
- It discovers the network and imports scanned data.
- Compatible with popular operating systems.
You can signup here .
Wrapping Up
So now that we have covered enough about the best ethical hacking tools of 2022, you can utilize these to harden up your website’s - or web app's - security and test the same for security vulnerabilities. Having queries? Tell us via the comments section below, we would be more than happy to resolve them.
People are also reading:
- Best Software Testing Tools
- What is Software Testing?
- Software Testing Interview Questions
- Penetration Testing Tools
- Automation Testing Tools
- Automated Browser Testing with Edge & Selenium
- Functional Testing Tools You Should Check for Automation Testing
- VoIP Testing Tools for Testing Network Performance
- Usability Testing Tools
- Agile Testing Tools to Develop high Quality Software





Leave a Comment on this Post